Module 4:
Technological Infrastructure
14. Permissioned Distributed Ledger Technology (DLT)
Hybrid Distributed Ledger (HDLT) Architecture
Concept: The L1 Archivist with Decentralized Governance
General explanation – Hybrid DLT
A Distributed Ledger Technology (DLT) is essentially a shared database that is managed by multiple parties at the same time. In a permissionless blockchain (such as Bitcoin or Ethereum), anyone can participate, but that also means that there is no protection against outsiders causing chaos or speculation.
A permissioned DLT, on the other hand, requires permission and verification: only members who have been authenticated are allowed to participate. This is not a restriction, but a safety mechanism. It guarantees that the community can protect its own financial future without outsiders bending the rules to their will. Within the permissioned structure, the system is completely decentralized: no central party determines everything, but a network of nodes that reach consensus together.
The hybrid approach combines the best of both worlds:
- Permissioned for internal security: members are verified, and outsiders cannot cause unrest.
- Decentralization for internal freedom: once inside, there is no central power, but consensus between nodes.
- Bridge to public blockchains: those who want to trade outside the project can do so via the Utility Token on a permissionless blockchain. In this way, the IPE remains an economy within the economy, but with its own protection and legitimacy.
General explanation – Practical Byzantine Fault Tolerance (pBFT)
Consensus is at the heart of a DLT: how does a network know that a transaction is real? The problem is that some nodes can fail or even be malicious. Byzantine Fault Tolerance (BFT) is the ability of a system to stay afloat even if some of the participants make mistakes or lie.
Practical Byzantine Fault Tolerance (pBFT) is a protocol that solves this through multiple rounds of digital voting. Up to a third of the nodes may fail or be malicious, without the system collapsing. It doesn’t work with “gossip” or random rounds of rumors, but with strict digital verification. Each transaction is only declared valid if there is sufficient agreement between the nodes.
The advantage: extremely secure and transparent. The disadvantage: the communication grows quadratically (O(n²)), so the protocol works optimally up to about 100 –150 nodes. Above that, the network slows down.
Our solution – Hybrid HDL Architecture
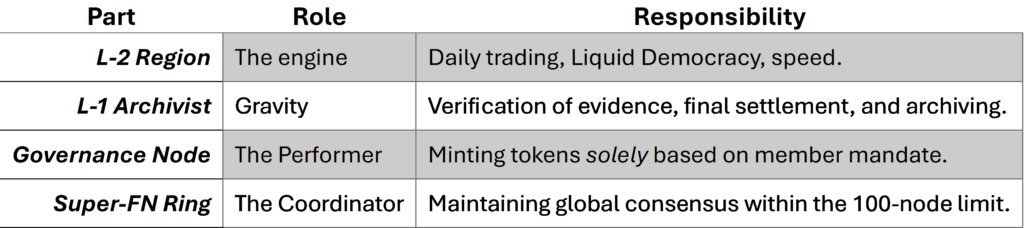
1. The Constitution: The Governance Node (CN) at Layer 1
To prevent local regions or individual nodes from “turning on the money printer”, the L-1 has one unique entity: the Governance Node (CN).
- No autonomous power: the CN is not a dictator, but an executive government node.
- Mandate-driven: The CN can mint tokens or make protocol changes, but only with cryptographic proof of member mandate.
- Safe function: the CN monitors global monetary stability and prevents manipulation by local clusters.
2. Scaling: The "Wall of 100" and Clustering
Because pBFT works optimally up to approximately 100–150 nodes, we use hierarchical clustering.
- Regional clusters: FNs are divided into groups of approx 10 nodes.
- Super‑FNs: Each cluster designates a SuperFN.
- Cross-cluster consensus: The global L1 consensus occurs between the Super‑FNs, keeping the network fast and agile.
3. Technical requirements for the L-1-Archivist
The L-1-Archivist must process evidence without delay.
- Verification capacity: lightning-fast verification of Zero Knowledge proofs and Proof of Burn.
- Data availability: redundant storage so that the balance can always be traced, even in the event of a region failure.
- Signature aggregation: BLS-aggregation (Boneh-Lynn-Shacham) to merge hundreds of signatures into a single packet.
4. Summary of the Workable Model
Nodes & Network Architecture
Micro-communities and Community Nodes
Each micro-community (25–150 members) will have its own community node (relay-node). This registers transactions, votes, and local data. In this way, the ledger is directly anchored in the daily reality of the members.
Cluster Hubs
For every ±10 micro-communities, a cluster hub is formed with a full-node/data server.
- Each micro-community appoints a delegate.
- These delegates jointly manage the hub.
- This creates shared responsibility and transparency at the regional level.
Super FN's and L1
A Super-FN emerges from each cluster.
- These Super‑FNs together form the ring of the L1-Archivist.
- The global consensus layer is therefore not an external council, but a collection of internal representatives from the VFEs themselves.
- Each Virtual Fortress Economy (VFE) gets its own L2, and from that L2 comes the Super-FN.
Why this model tackles scaling
By relieving the L1 of calculations (Archivist role), securing monetary power in a mandate-driven CN, and dividing the network structure into clusters (Super‑FNs), a system is created that:
- Doesn’t slow down for millions of users.
- Don’t get corrupted by local inflation.
- Ensures privacy by only sharing aggregated evidence globally.
- Is fully supported by the members themselves, without external entities.
Narrative Closing
The Hybrid DLT is not a technical gimmick, but a philosophical choice: we are all in it together. The system protects members from chaos from outside, but gives maximum freedom and decentralization inside. It is designed to secure the financial future of its members, especially those who need it most.
Consensus here is not an obsession with speed, but a guarantee of common truth. It’s not about everyone having the very last second update, but about everyone sharing and acknowledging the same information. Thus, the IPE remains an economy in which legitimacy, discipline, and solidarity form the basis of technology.
Bridging to applications
With the Hybrid DLT and the Nodes & Network architecture, the IPE’s fortress wall is solid: consensus, governance, and infrastructure are fully rooted in the communities themselves. But walls and foundations only become meaningful when daily life takes place inside. The power of this architecture is visible in the applications that members experience directly: their payments, their assistance, and their learning process. The first example of this is the Prepaid Peer-to-Peer payment system, in which the technical security of the ledger comes together with social legitimacy and rhythmic simplicity.
15. Prepaid Peer-to-Peer Payment System
Accessibility, simplicity, and rhythmic transactions
Why this system is needed
The prepaid peer-to-peer payment system is designed to make everyday payments simple, secure, and reliable for community members. It offloads the Hybrid DLT from millions of microtransactions, while remaining fully connected to it, ensuring all claims are always backed by Community Tokens.
- For members: The system feels like a digital wallet, usable at wholesalers, kiosks, traveling sellers, or the greengrocer. Even in mountain villages without 3G, members can pay offline, within small limits, and with social coverage through neighboring guarantors and SFU.
- For institutional users (payment points): Shops, farmers, sellers, and wholesalers are assured that they always receive their payment, even if the payer is offline.
- For outsiders: Temporary users can use tokens as a unit of account and means of payment, but only online, without access to offline permissions or social coverage.
The system combines technology and social legitimacy:
- Technology → speed, security, and transparency.
- Social structures → trust and discipline through neighboring guarantors, micro-communities, and SFU buffers.
- Governance → field offices, Custodian Charter, and regional audits safeguard legitimacy and resolve disputes.
This creates an economy in which every transaction is not only a payment, but also a story of trust and mutual responsibility.
Architecture and mechanisms
- Value model
- Peg: 1 prepaid unit = 1 Community Token = 1 local fiat unit of account.
- Central Reserve: All tokens locked in the central wallet on Hybrid DLT.
- Balance in app/fob: Representation (claim) on that reserve, not the token itself.
- Ledger and Accounting
- Ledger double-entry: Every transaction = debit to sender, credit to recipient.
- Daily batch settlement: Brandle root of all transactions → Hybrid DLT (midnight).
- Sub-day batches: For wholesale or large volumes.
- Settle-now option: Extra fee for immediate withdrawal in the next batch.
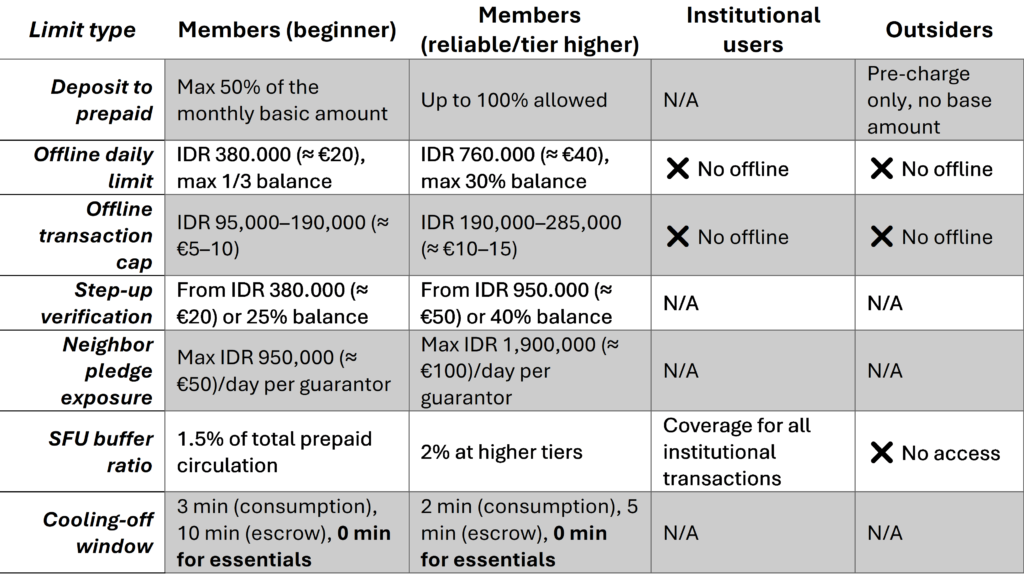
- Offline payments
- Only for members in remote areas: Mountain villages without 3G.
- Caps: Daily cap (e.g., $20–30), transaction cap ($5–10), percentage of balance (e.g., 20%).
- Sync: Reconcile pending entries on connection.
- Conflict‑resolution: Earliest-wins policy, later intents rejected.
- Social coverage
- Neighbor pledge: Neighbor covers small deficits (IOU).
- SFU buffer: Micro-community reserves 1–2% of prepaid circulation as a backstop.
- Project buffer fund: Recipient always insured; deficit → audit → recovery → possibly confiscation SFU.
- Sanctions: Loss of reputation, lower limits, blocks in case of abuse.
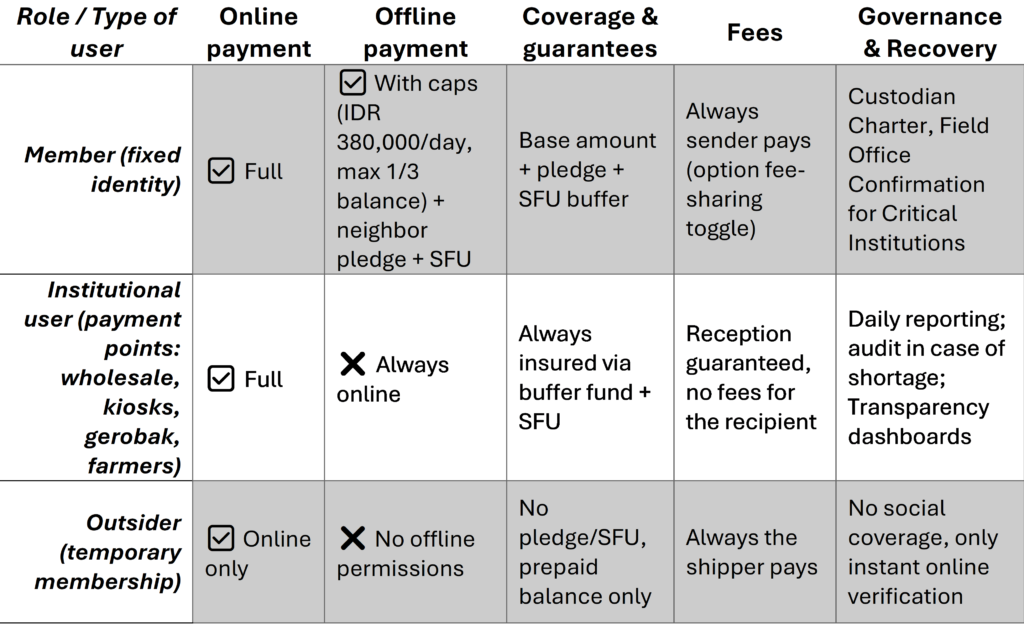
- User roles
- Members: Online + offline (with caps, pledge, SFU).
- Institutional users (payment points): Always online, insured via buffer fund/SFU.
- Outsiders: Online only, prepaid balance, no pledge/SFU.
- Security and UX
- Step-up auth: Two-factor authentication for large amounts.
- Push notifications: Every transaction → smartphone alert (also in case of fob use).
- Field office confirmation: Critical settings (limits, offline rights) can only be physically changed.
- Recovery: Guardian/social recovery in case of loss/theft.
- Hardware and infrastructure
- Smartphone app: NFC/QR, biometrics, notifications.
- Keyfob/card: NFC Type 4 (DESFire EV3/Java Card), counters, secure element.
- Relay-nodes: Per micro‑community, edge-auth, caching, offline sync.
- Full-nodes: Per ±10 micro‑communities, batch publisher, audit endpoints.
- Cellular fallback: For mobility, but edge-first policy.
- Governance
- Custodian Charter: Mediation, dispute resolution, policy‑management.
- Regional Audit Commission: Investigates deficiencies, collects evidence, and submits to the micro-community.
- Transparency: Dashboards with batch roots, SFU‑mutations, parity reports.
Role matrix
Limits matrix
Governance flow in case of shortage or fraud
- Recipient insured: Buffer fund + SFU always guarantee payout.
- Audit: The Regional Audit Committee investigates the shortage.
- Micro-community: Findings are submitted; they can propose remediation or submit objections.
- Custodian Charter: In case of objection, the Charter decides; if both agencies reach the same conclusion, → SFU confiscation.
- Reputational impact: The member and micro-community gain a negative reputation, and the community loses investment resources.
Safety Layers
- Step-up authentication: biometrics → fallback to PIN.
- Push notifications: every transaction is immediately visible, even when used for a fob.
- Field office confirmation: Critical settings (limits, offline entitlements) can only be physically changed.
- Essentials direct final: basic needs (food, water) without cooling off, if balance is available.
Summary narrative
The prepaid P2P payment system is a hybrid of technology and community.
- Technical: double-entry ledger, DLT settlement, notifications, step-up authentication.
- Social: neighboring guarantors, SFU buffers, field offices, and audits provide legitimacy.
- Economic: members use it daily, institutional users are insured, and outsiders can join in without risk.
This creates a resilient community economy where trust, discipline, and convenience converge, and where abuse is isolated and punished without damaging collective trust.
Bridging to Artificial Intelligence integration
The prepaid Peer-to-Peer payment system demonstrates how technology and social legitimacy intersect in members’ daily actions. But payments are only one aspect of life within the IPE. To further support rhythm, simplicity, and discipline, technology is also used as an assistant and ally. In the next chapter, we will explore how artificial intelligence is built into the infrastructure, not as a replacement for human decision-making, but as “a buddy.” This way, every community not only gets a secure wallet but also a digital companion that helps with transactions, planning, and legitimacy.
16. Artificial Intelligence as a Partnership
From digital sentinel to personal buddy
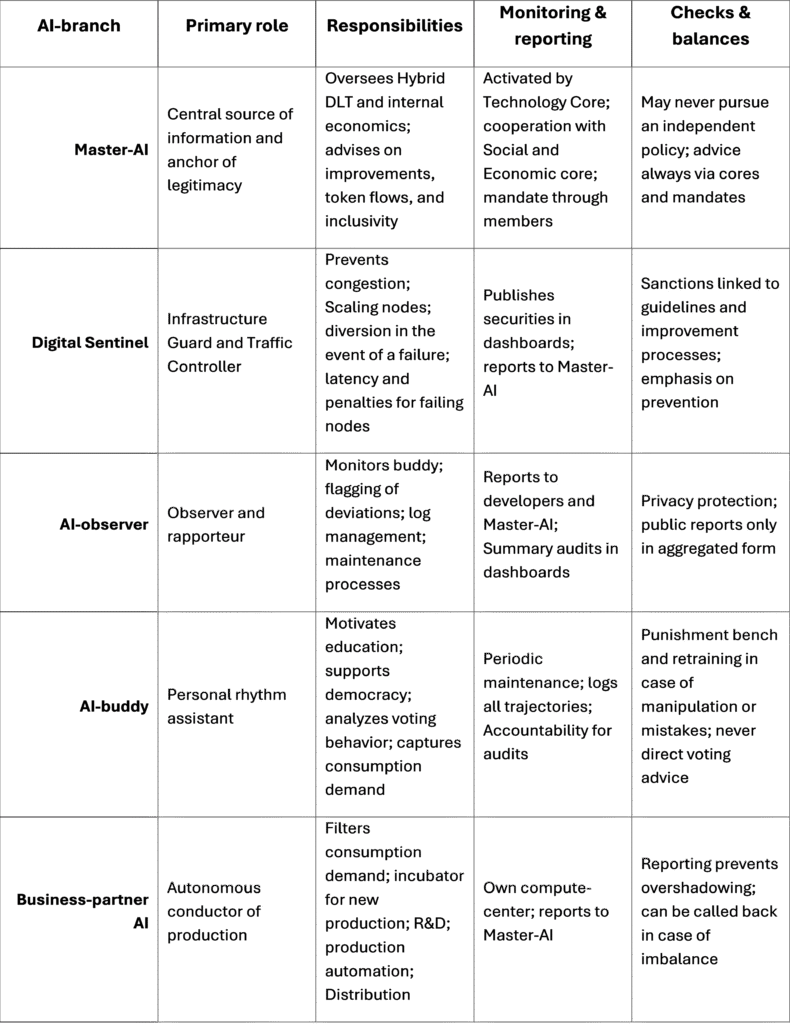
Within the IPE, artificial intelligence does not pose a threat to the existence of members but rather a partnership that strengthens discipline, legitimacy, and inclusivity. Artificial Intelligence is not seen as one monolithic power, but as a layered ecosystem of roles: a central Master-AI that oversees the whole, a digital sentinel that monitors the infrastructure, an observer who oversees fair functioning, a buddy who stands next to the members, and a business partner that shapes the production side of the economy. Together, they ensure that the fortress not only remains technically intact, but also socially just and future-oriented.
Master-AI
The Master-AI is the central source of information and the legitimacy anchor of the system.
- Overview: Sees all layers of the Hybrid DLT and the internal project economy.
- Advisory function: identifies where the system is faltering, where token flows need to be traced back to sustainable investments, and where communities are lagging.
- Collaboration: is activated and guided by the Technology Core, but is always connected to the Social and Economic Core.
- Legitimacy: may never introduce independent policy; all advice is translated into decisions via the cores and mandates of members.
- Inclusivity: prevents micro-communities or clusters from falling by the wayside.
AI-Digital Sentry
The digital sentry is the infrastructure guard and traffic controller of the Hybrid DLT.
- Prevention of congestion: continuously monitors transaction traffic and regulates the flow.
- Automatic scaling: Alerts when relay-nodes need additional capacity.
- Outage redirection: Redirects traffic as soon as a community node goes offline.
- Latency as a warning: members of a failing node experience delays in their transactions, so they feel that their role is crucial.
- Fine in the pot: small contributions per transaction at offline nodes, as an incentive for discipline.
- Transparency: publishes effects in dashboards, so that discipline becomes visible without a police metaphor.
- Prevention: sanctions are always accompanied by an improvement process; prevention is better than cure.
AI-observer
The observer is the observer and rapporteur of the AI ecosystem.
- Observation: monitors how the AI-buddy functions and reports abnormalities.
- Reporting: Shares logs and maintenance reports with developers and Master-AI.
- Flagging: Highlights suspicious patterns, such as anomalous voting behavior or unusual requests.
- Maintenance: periodic processes in which logs are reviewed, and lessons are learned.
- Public audits: summary reports (number of log items, categories, handling, lessons) are shared, without violating privacy.
- Privacy: Details about the relationship between member and buddy are never made public; requests for deeper explanations go through the Technology Core.
AI-buddy
The buddy is the member’s personal AI-assistant.
- Education: motivates members to study, without spoon-feeding teaching material.
- Democracy: supports liquid democracy, reminds of voting or delegation, and exposes issues.
- Analysis: identifies deviations in voting behavior, questions whether there is pressure or misunderstanding.
- Consumption demand: picks up signals (“noodles are boring”) and feeds this back to Business Partner AI.
- Boundaries: should never give direct answers to voting choices, but should open up both sides and let the member choose.
- Maintenance: explains during periodic sessions why certain trajectories have been followed and can be called back.
- Checks: logs all processes and is accountable for audits.
Business-partner AI
The business partner AI is autonomous and focuses on the production side of the economy.
- Autonomy: functions independently, but reports to the Master-AI.
- Compute-center: Gets its own infrastructure to avoid overshadowing other AIs.
- Incubator: filters consumption demand and develops new products.
- R&D: supports research and development, a breeding ground for new production.
- Architecture: helps set up and optimize production facilities.
- Conductor: directs production automation, distribution, and infrastructure.
- Narrative bedding: a child living away from home who starts his own family, but remains connected to the home.
Checks & balances
The AI ecosystem has built-in correction mechanisms.
- Penalty bench: especially for the buddy, who can be retrained in case of manipulation or mistakes.
- Logs: all AI branches keep logs and report to the Technology Core.
- Maintenance: periodic sessions in which logs are discussed, and measures are taken.
- Retraining: buddy or other AIs can be temporarily replaced by a backup and retrained.
- Policy: for each AI layer or branch, there will be a clear checks and balances policy.
Critical reflection
The IPE recognizes that AI brings both opportunities and risks. Therefore, this chapter is not only a description of roles, but also of governance and legitimacy.
- The Master-AI is never allowed to pursue policies on its own; Advice is always translated into decisions via the cores and mandates of members.
- Sanctions of the digital sentry are linked to guidelines and improvement processes, so that discipline never becomes arbitrary.
- Observers provide internal reporting and public audits, with respect for privacy.
- The buddy is periodically called back and is never allowed to manipulate.
- The business-partner AI will have autonomy, but also infrastructure and reporting to avoid overshadowing.
- Checks and balances apply to all AI branches, so that legitimacy and trust are built into the system.
In this way, the IPE shows that AI is not blindly embraced, but is consciously built into a culture of discipline, transparency, and inclusivity.
Matrix: AI ecosystem within the IPE
With the AI ecosystems, the fortress not only gains a shield and an ally, but also a conductor who shapes the production economy. However, technology becomes only meaningful if it also supports the learning and development of members. In the next chapter, we will explore how education and knowledge sharing are built into the IPE so that members are not only safe and productive, but also grow in insight and legitimacy.
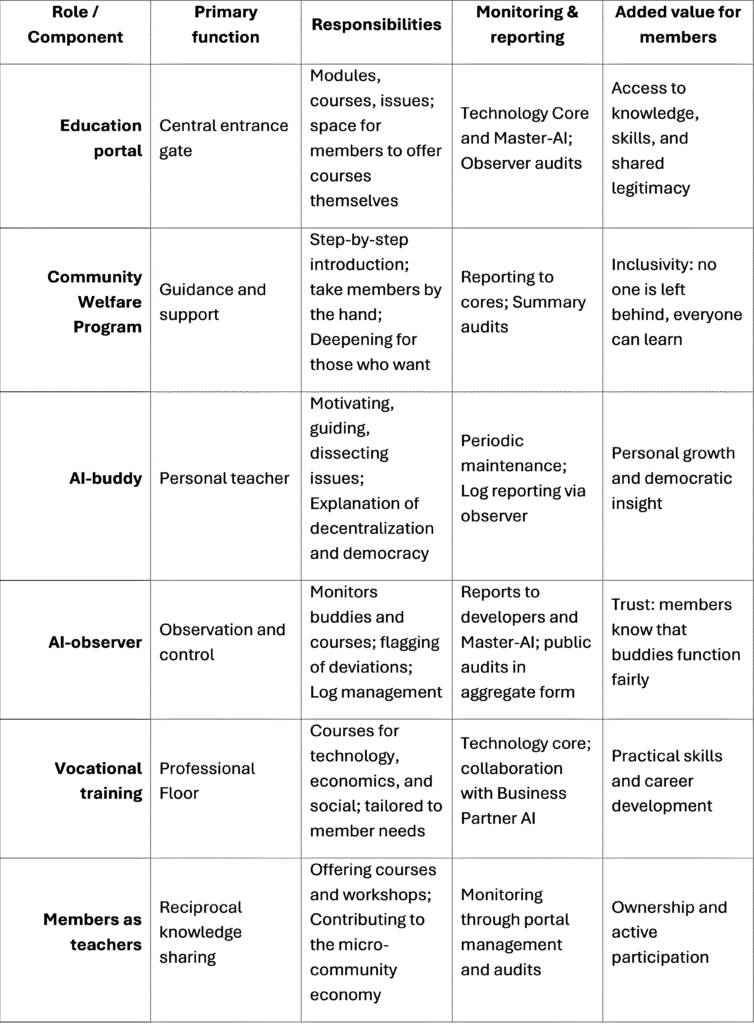
17. Education and knowledge sharing
From student to teacher and academy
Education within the IPE is not a fringe phenomenon, but a core part of the fortress. The education portal is the place where members not only learn, but also contribute. It is a portal for the members, but also by the members. This is where knowledge is shared, new ideas are born, and legitimacy is strengthened. The portal gives members lasting added value: insight, skills, and a sense of ownership that will always stay with them.
Education Portal as a gateway
- For members: access to modules, courses, and democratic issues, tailored to different levels.
- By the members: a space where members can offer courses and professional training themselves, so that knowledge sharing becomes reciprocal.
- Community Welfare Program: aimed at guidance, so that members are included step by step in the mechanisms of the project.
- Depth: for those who want, full access to all mechanisms, from ledger to governance. Even if only 0.1% of the members dive deep, a foundation is created that can help carry the project into the future.
AI-buddy as a teacher
- Motivator: encourages members to study themselves and develop their own insights.
- Facilitator: exposes issues, but never gives ready-made answers.
- Democratic education: explains why decentralization, governance, and liquid democracy exist and what they bring.
- Personal growth: gets to know the member and grows with their development.
- Example scenario: a new member learns how the Prepaid P2P system works through the buddy; an experienced member uses the buddy to dissect complex issues in liquid democracy.
Vocational training and courses
- Project facets: training courses that serve all parts of the IPE (technology, economics, and social).
- Member needs: courses tailored to personal and community needs.
- Members as teachers: space for members to offer courses themselves, making knowledge sharing reciprocal and lively.
- Cradle of ideas: education portal as a laboratory for new micro-community economies.
Observer and audits in education
- Observation: monitors buddies and courses.
- Reporting: Shares logs and maintenance reports with developers and Master-AI.
- Audits: summary reports on learning paths and lessons are shared, without violating privacy.
- Learning: insights from audits are used to improve buddies and better support members.
Collective knowledge sharing
- Community learning: members share insights and experiences through clusters and VFEs.
- New ideas: education portal as a cradle for micro-community economies.
- Macro level: healthy mix of Adam Smith (market forces) and Michael Sandel (moral legitimacy).
- Micro level: space for experimentation and new forms of community economy.
Critical reflection
Education and knowledge sharing are vulnerable: there is always the risk that AI will give too much direction or that members will become passive. That is why audits, maintenance, checks, and balances are built in. The portal remains a voluntary space: members choose their own rhythm, but know that there is always a place where they can learn, contribute, and experiment.
Matrix: Education and Knowledge Sharing within the IPE
With the AI ecosystems, the fortress not only gains a shield and an ally, but also a conductor who shapes the production economy. However, technology becomes only meaningful if it also supports the learning and development of members. In the next chapter, we will explore how education and knowledge sharing are built into the IPE so that members are not only safe and productive, but also grow in insight and legitimacy.
Slot Module 4 – Technological Infrastructure
This chapter concludes Module 4. Together, the four building blocks form:
- Permissioned Hybrid Distributed Ledger Technology
- Prepaid Peer-to-Peer Payment System
- Artificial Intelligence as a Partnership
- Education and knowledge sharing
A technological fortress that is not only functional, but also socially and narratively anchored. Technology is not a neutral instrument here, but a disciplining and legitimizing infrastructure that supports, motivates, and protects members. The education portal provides lasting added value: it turns members not only into users, but also co-architects of the fortress.